Cybersecurity Essentials establish the baseline for defending modern technology environments against evolving threats, shaping resilient operations across industries and regions and global markets worldwide. In today’s complex ecosystem, people, processes, and technology must blend into a cohesive defense that protects data, operations, and trust across cloud, on-prem, and hybrid infrastructures, with measurable outcomes that matter to risk governance and executive strategy—this mindset supports resilience, compliance, and ongoing optimization. A practical framework of governance, risk management, and repeatable controls helps teams reduce risk and support secure digital transformation by aligning security with business goals, to empower proactive defense, improve audit readiness, and support supplier and regulatory requirements. Among the core concepts, zero trust architecture guides access with continuous verification and adaptive policies. By weaving threat detection and response into daily operations, organizations can detect anomalies earlier and respond faster to incidents, while aligning security with business priorities and stakeholder expectations today.
In other words, cybersecurity fundamentals form a coordinated program that protects data, people, and operations across changing technology stacks. A risk-based security posture prioritizes governance, continuous monitoring, and resilience over one-time fixes. Defensive layers like identity governance, secure configurations, and organized incident response create a scalable defense that grows with cloud use and device diversity. This approach emphasizes people and culture alongside technology, ensuring security becomes a shared responsibility across the organization. By aligning policy, practice, and measurement, teams can sustain trust while pursuing digital innovation.
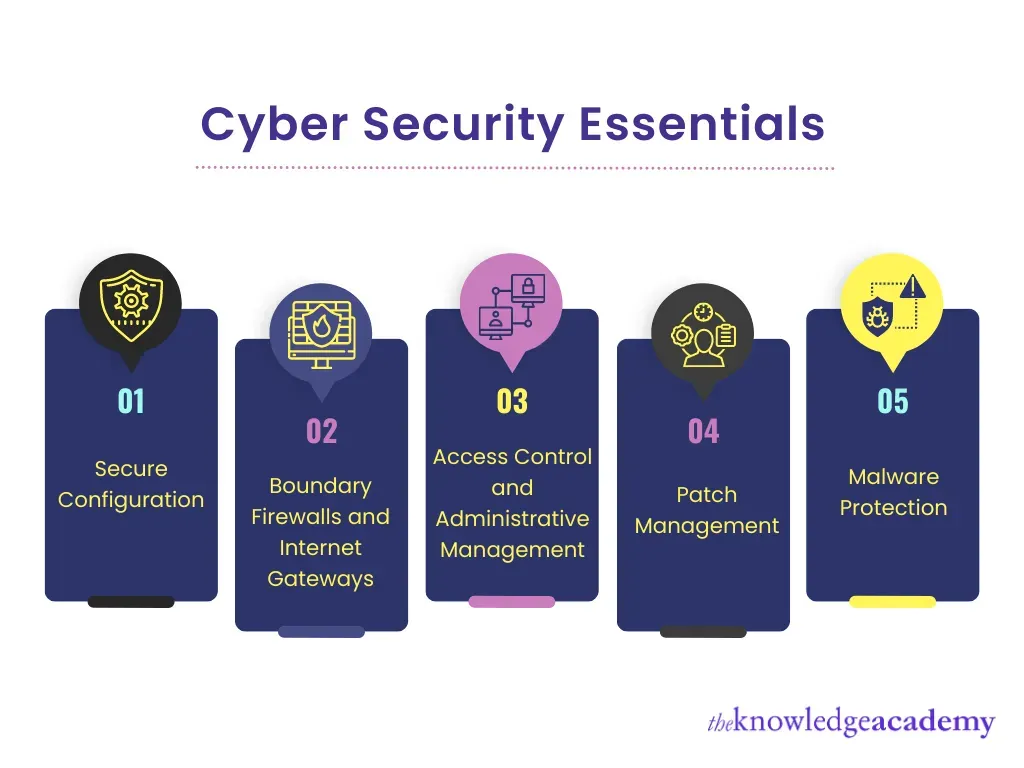
Cybersecurity Essentials Framework for Modern Technology Environments
A solid cybersecurity program rests on a core framework that scales across diverse technology stacks found in modern technology environments. Foundational pillars include identity and access management, threat detection and response, data protection, secure software development, network security, and continuous monitoring. When governance, risk management, and security operations align with practical controls, organizations gain resilience against evolving threats.
To operationalize this framework, teams document security best practices and implement repeatable processes that reduce variability. Regular assessments, baseline configurations, patch cycles, and automated monitoring help maintain a strong security posture as technology environments evolve. The result is predictable protection and faster, more coordinated responses to incidents.
People, Process, and Technology: The Three Pillars of Cybersecurity Essentials
Cybersecurity Essentials depend on the three interlocking pillars: people, processes, and technology. Security awareness training, role-based access controls, and phishing simulations reduce human error and build a culture of accountability. Leadership sponsorship and clear incident reporting channels elevate security to an organizational priority.
With governance guiding risk assessment and incident response playbooks, processes provide a map for action during events. When change management and vulnerability management are integrated with the right tools—endpoint protection, CSPM, and secure configuration baselines—technology becomes a force multiplier for defense in depth.
Identity and Access Management: The Cornerstone of Zero Trust Architecture
Zero Trust Architecture is the cornerstone of modern identity governance. The premise never trusts by default; it verifies every access request through strong identity verification, least-privilege principles, and continuous risk assessment of sessions. This approach helps prevent attackers from moving lateral movement after a breach.
Practical implementations include centralized identity management across cloud and on-prem resources, just-in-time provisioning, time-bound access elevation, adaptive access policies, and encryption of data at rest and in transit. A key outcome is a reduced attack surface even when credentials are compromised.
Network Security and Segmentation: Containing Compromise in Modern Technology Environments
Network Security and Segmentation are essential to containment in modern technology environments. Proper segmentation limits the blast radius, allowing security teams to isolate affected workloads and preserve business continuity. Micro-segmentation enforces least-privilege communication between workloads and strengthens overall resilience.
Complementary controls include secure remote access with encrypted tunnels and context-aware authentication, regular reviews of firewall rules and security group configurations, and continuous monitoring for anomalous traffic patterns. By maintaining tight segmentation, organizations can detect and contain threats before they spread.
Threat Detection and Incident Response: Stopping Breaches with Security Automation
Threat Detection and Incident Response provide the rapid feedback loop needed to stop breaches before they escalate. A mature capability blends security monitoring, analytics, and practiced workflows to identify incidents early and guide containment.
Core components include centralized security analytics across endpoints, networks, and cloud resources; real-time alerting with triage processes; and playbooks that automate routine containment and remediation steps where feasible. Regular tabletop exercises validate readiness and improve cross-team coordination, strengthening overall security posture and resilience.
Data Protection, Privacy, and Compliance in the Age of Security Automation
Data Protection, Privacy, and Compliance form the data-centric core of Cybersecurity Essentials. Encryption, key management, and robust data governance ensure sensitive information remains confidential and accessible only to authorized users. Practices like data loss prevention, data classification, and tested backups support resilience against ransomware and data corruption.
Regulatory alignment and privacy-by-design principles help organizations meet legal obligations while maintaining business agility. Ongoing audits, transparent security metrics, and governance dashboards support accountability, driving security improvements and reinforcing trust with customers, partners, and regulators. In a world powered by security automation, governance remains essential to ensuring continuous compliance as technologies evolve.
Frequently Asked Questions
What are Cybersecurity Essentials for modern technology environments and why are they important?
Cybersecurity Essentials are a set of core practices that blend people, processes, and technology to defend modern technology environments. They cover identity and access management, threat detection and response, data protection, secure software development, network security, and continuous monitoring to reduce risk and improve resilience.
How does zero trust architecture fit into Cybersecurity Essentials?
Zero trust architecture is a central pillar of Cybersecurity Essentials. It follows the principle of never trust, always verify, with strong identity management, least-privilege access, MFA, adaptive access policies, and continuous risk assessment to limit lateral movement after a breach.
What is threat detection and response within Cybersecurity Essentials?
Threat detection and response combines security monitoring, analytics, and practiced workflows to identify breaches early and respond swiftly. Key components include centralized analytics across endpoints, networks, and cloud resources, real-time alerts, incident response playbooks, and regular tabletop exercises.
What role does security automation play in Cybersecurity Essentials?
Security automation scales defenses in modern technology environments. It reduces manual toil, accelerates response, and enforces security best practices through SOAR playbooks, automated patch management, configuration drift detection, and continuous monitoring.
What are best practices for Identity and Access Management in Cybersecurity Essentials?
Identity and access management is the cornerstone of Zero Trust and Cybersecurity Essentials. Implement centralized identity across cloud and on‑prem resources, enforce MFA, practice least-privilege access, use just-in-time provisioning, and continuously assess session risk.
What is a practical roadmap to implement Cybersecurity Essentials?
A practical roadmap starts with a current-state assessment and a phased rollout: establish identity governance and MFA, deploy threat detection and response, enforce zero trust and micro-segmentation, introduce security automation, and strengthen data protection and governance. Measure progress with metrics like MTTD, MTTR, MFA coverage, patch compliance, and data protection coverage.
| Pillar / Topic | Key Points |
|---|---|
| Cybersecurity Essentials Framework | Foundational pillars: identity and access management; threat detection and response; data protection; secure software development; network security; continuous monitoring. Applies to on-prem, multi-cloud, or hybrid environments. |
| People, Process, and Technology: The Three Pillars | People: security awareness, role-based access, phishing simulations; Process: governance, risk assessment, incident response; Technology: defense in depth tools, CSPM, secure baselines. |
| Identity and Access Management (IAM) / Zero Trust | Never trust, always verify; strong identity controls, least-privilege, MFA, adaptive access; centralized identity management; just-in-time provisioning; continuous risk assessment; data encryption at rest and in transit. |
| Network Security and Segmentation | Segment networks to limit blast radius; micro-segmentation; secure remote access; review firewall rules; continuous anomaly monitoring. |
| Endpoint Protection and Secure Configuration | Next-gen antivirus/EDR; patching; secure baselines; privilege management. |
| Threat Detection and Incident Response | Centralized analytics; real-time alerting; escalation paths; playbooks; tabletop exercises. |
| Security Automation and Continuous Monitoring | Automation reduces toil; SOAR playbooks; baseline behavior models; continuous monitoring; proactive threat hunting. |
| Data Protection and Privacy | Encryption; key management; DLP and data classification; backups and tested restores; regulatory alignment. |
| Governance, Risk, and Compliance | Align with standards (NIST, ISO/IEC 27001); transparent metrics; audit readiness; risk posture communicated to executives and boards. |
| Roadmap for Implementing Cybersecurity Essentials | Phased approach: identity governance, baseline configurations, MFA; threat detection/EDR; zero trust and micro-segmentation; security automation; data protection and governance; measure with MTTD/MTTR, MFA coverage, patch compliance. |
Summary
Conclusion: Cybersecurity Essentials provide a comprehensive blueprint for protecting data, operations, and trust across modern technology environments. By balancing people, processes, and technology, organizations build a resilient security posture that scales with cloud, edge, and on-prem resources. A Zero Trust mindset, robust threat detection, endpoint protection, and automation empower teams to detect, contain, and recover from incidents more quickly. When implemented as a phased roadmap with governance and continuous improvement, Cybersecurity Essentials help organizations reduce risk to manageable levels while enabling secure innovation and stakeholder confidence.